You try to connect to a computer on your Windows network (using what is now called “Windows File Sharing”). Instead of a login prompt, you are greeted with an error message that reads: “The referenced account is currently locked out and may not be logged on to“.
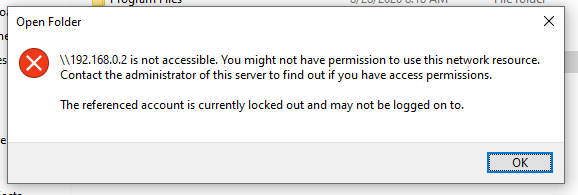
This error can only occur if you’ve set an account lockout policy, which locks your account after several failed login attempts (this is recommended by Microsoft). But how could there be a failed login attempt if you were never asked for your user name and password in the first place?
Here’s how. When you connect to a network share, before you get the chance to type in your user name and password, Windows will try to log on with your credentials from your current computer.
Let’s say your local user name is “Clara”. If the target computer also has a “Clara” account, but with a different password, the autologin fails. Furthermore, Windows appears to retry the operation a few times (God knows why) and this may be enough to trip up the account lockout mechanism. (As a quick confirmatory experiment, I just set my account lockout to 5 failed attempts and tried to connect to it – I was locked out after the first failed autologin.)
Of course, a lockout means you’re screwed. You cannot try again with the correct password. Worse, you cannot even log on to the other computer locally. You have to wait whatever the lockout duration is set to – typically something like 15 minutes. On the plus side, you can use the break to do anything you like. I used mine to estimate what yield of a nuclear weapon would be enough to wipe out Redmond, WA.
Bad solution:
As you know from the previous post, renaming your account on one of the computers is not a good idea. Not only will it not solve the autologin issue, but it will also add enormous confusion.
Good solution:
Go to the Credential Manager and add the user name and password for the target computer. Now Windows will use these credentials automatically whenever you connect to that machine.
Thank you! It seems that server2022 has set the lock policy to 10 minutes by default.
KB5020282—Account lockout available for built-in local administrators
https://support.microsoft.com/en-us/topic/kb5020282-account-lockout-available-for-built-in-local-administrators-bce45c4d-f28d-43ad-b6fe-70156cb2dc00
It seems this only affects Windows 11. Windows 10 systems, or even Windows 11 systems upgraded in-place from Windows 10, don’t exhibit this behavior and will prompt for credentials in this case. Is there a way I can get this behavior on directly-installed Windows 11 systems?